Resources
Connect existing operations with real-time computer vision solutions for safety, productivity and ESG.
Collect
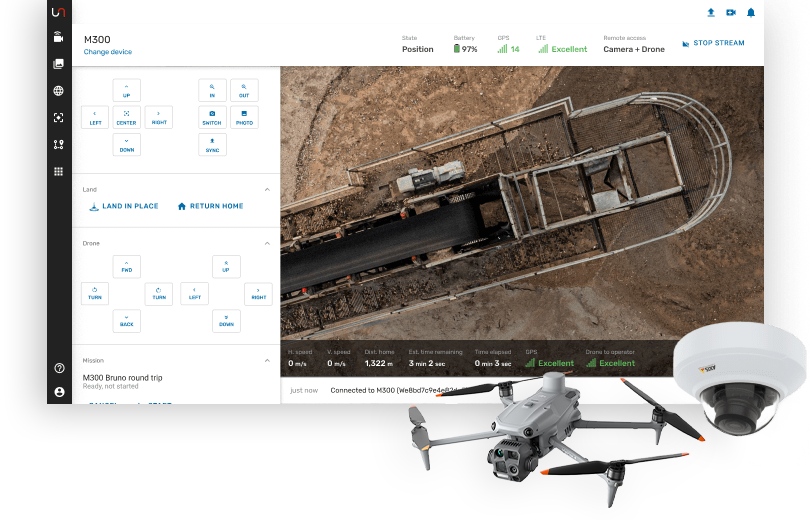
Operationalize live video from drones
and IP cameras to take control.
Analyze
Turn manual visual inspections into automated, reliable and action based events.
Action
Inject real-time data into your frontline operations for faster decision making through integrated dashboards and alerts.
Incorporate machine vision into your existing workflows
Deploy Unleash live in a modular approach
Extraction
Automated UAV surveying
UAV blast monitoring
GET missing tooth and tooth wear detection
Bucket payload monitoring
Fleet usage
Land management and rehabilitation for ESG
Site safety
Material Handling
Crusher analytics and boulder detection
Ore cart monitoring
Heavy vehicle analytics
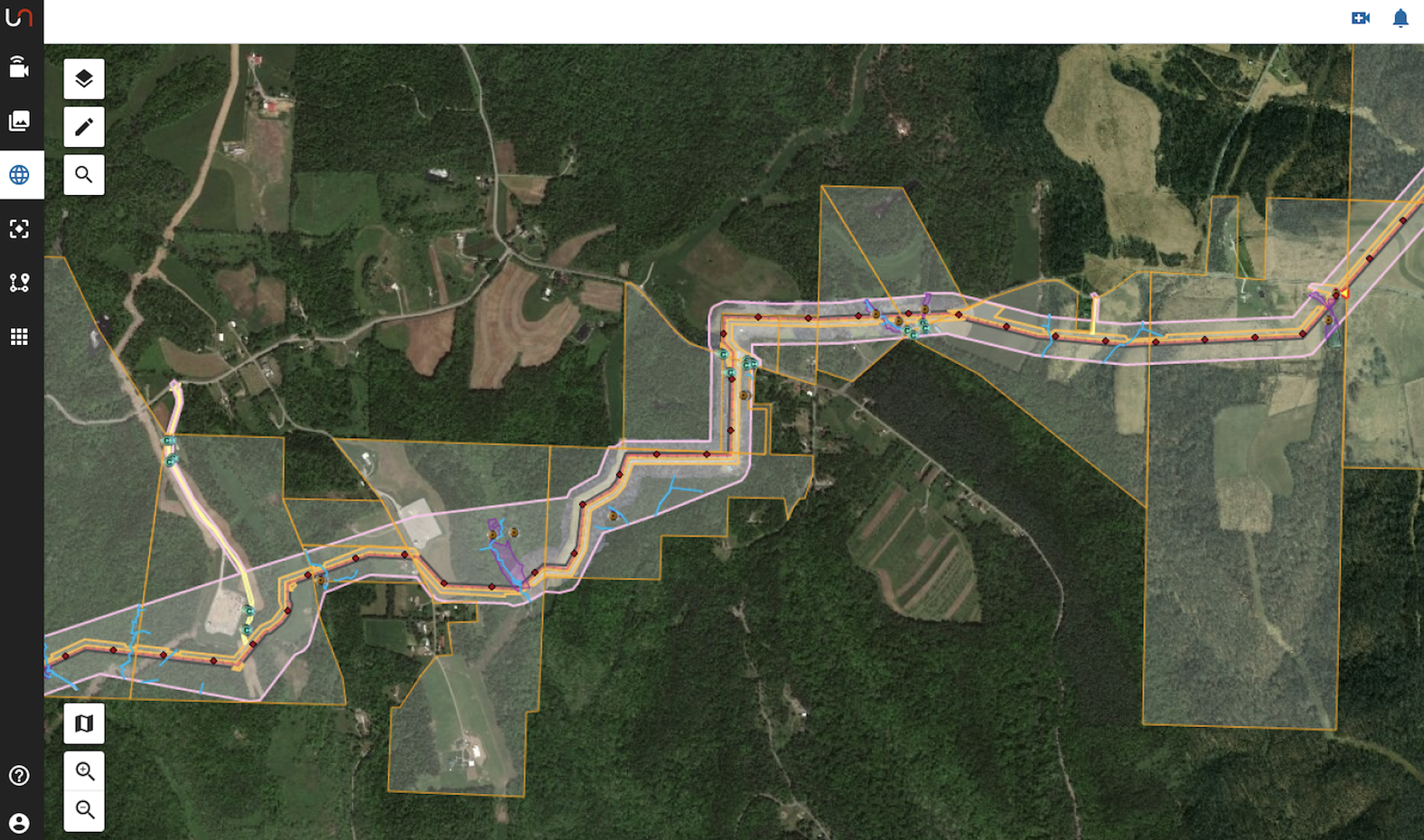
Linear pipeline monitoring
Linear conveyor monitoring
Rail performance monitoring
Rail-yard logistics
Hot Roller detection
Mineral Processing
Mine shaft analytics
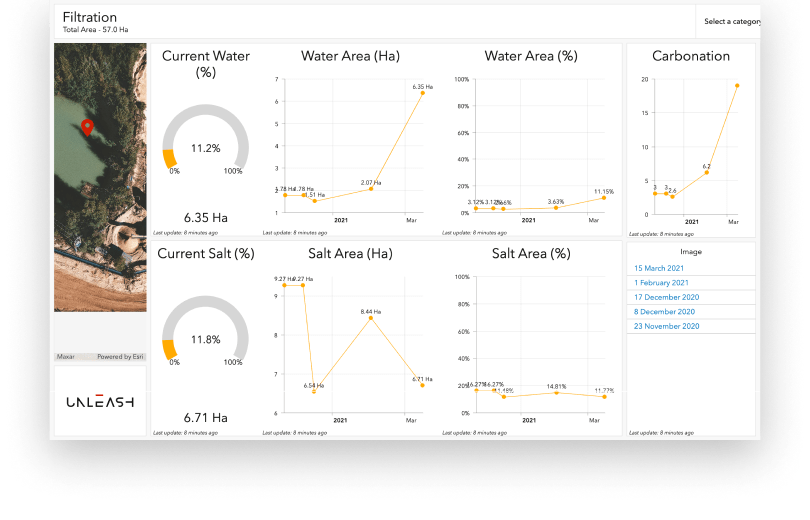
Filter press health monitoring and blowout prevention
Tailing dam stability and carbonation
Flaring and venting (Ringelmann)
Methane detection
Containment loss
Don’t see your use case listed?
Leverage Unleash live to deploy new capabilities

“We’ve looked at almost a dozen different options and Unleash live has come in as the best performer.
”
CASE STUDY
Crusher Insights
Reduced the rate of crusher failure and improve operations by implementing an automated solution to detect oversized rocks that cause machine failure on conveyor belts.
1 M+
Saved in costs
4 months
Wait time eliminated for conveyor belt replacement
CASE STUDY
Pipeline Inspection
Conducted efficient inspections with real-time collaboration, enabled by live streaming and building 2D Orthomosaics and 3D Point clouds.
3X
4X
Increase in efficiency
Reduction in cost
CASE STUDY
Filter Press
Recommended and deployed CCTV cameras and AI to provide constant monitoring, alerting and performance analytics for the filter press asset.
Reduced consumable cost and asset downtime
Prevent blowouts and unplanned maintenance
Security
Built on world leading infrastructure for secure and scalable deployment as well as ensuring data sovereignty requirements.
Read more
Latest blog posts on Resources